Hello Readers, Whats Up? Hope You all should be fine enough to read this tutorial. As in previous Article I said that i'll demonstrate that how to attack debuggable android applications. So This tutorial is about Finding and Attacking Debuggable Android Applications.
Before i start the procedure Let's collect the requirements.
- Android Emulator
- Vulnerable APK Application
- apktool
- jdb debugger
and as in previous tutorial i told that Android Tamer Have all these tools so no need to be worry just start up your android tamer and if you don't have , get it now.
Checking For Vulnerable Apps
First of all we need to learn that how to check if an app is vulnerable or no. to check this we need to find either the app is debuggable or no. and how to do it? Here comes the Role of UrduSecurity.
Just Download the vulnerable apk file from above given link and provide following command in your android tamer's terminal .
- apktool d Vulnerable.apk
after You have done it, You have to Check AndroidManifest.xml File in order to see either the app is debuggable or no. Provide the Following Command to do that.
- nano Vulnerable/AndroidManifest.xml
Exploiting the Vulnerable Application
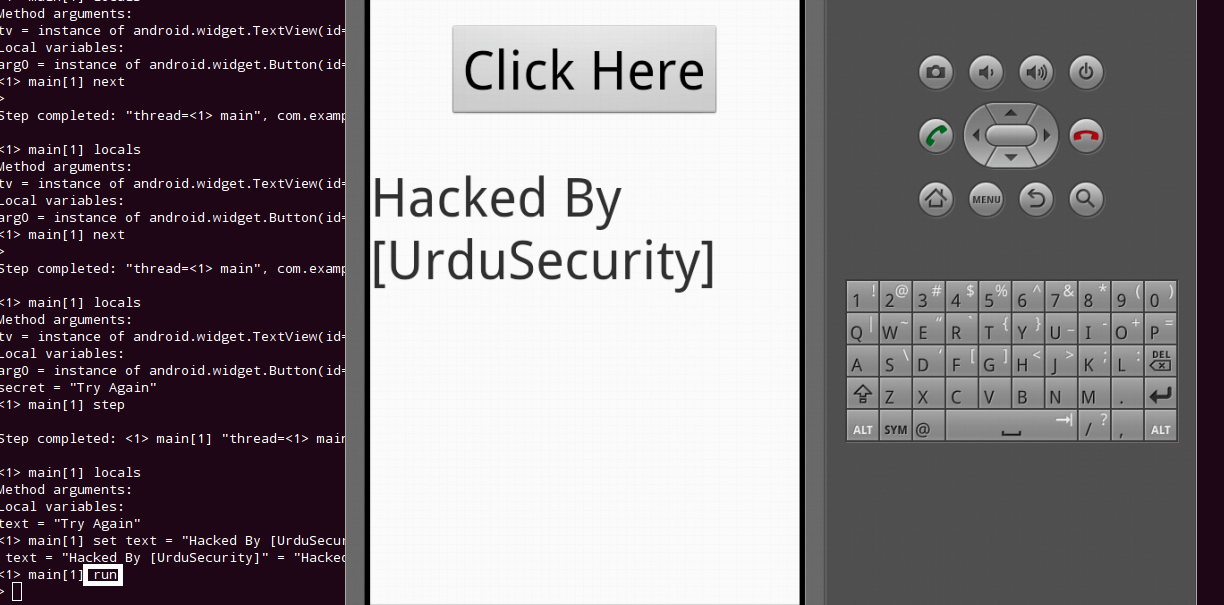
Now that You've got a vulnerable android app, Let's exploit it. start up your android emulator and launch the application. your goal is to change the text Try Again into Hacked By [UrduSecurity]. but first we have to check dalvik vm ports listening on emulator. give following command.
- adb jdwp
okay now we have to find on which port our Vulnerable.apk is listening which you can find again by running the app and enumeratng the ports. Let's assume the app is litening on 1180 port so let's forward to this port and attach our terminal to the app using jdb debugger.
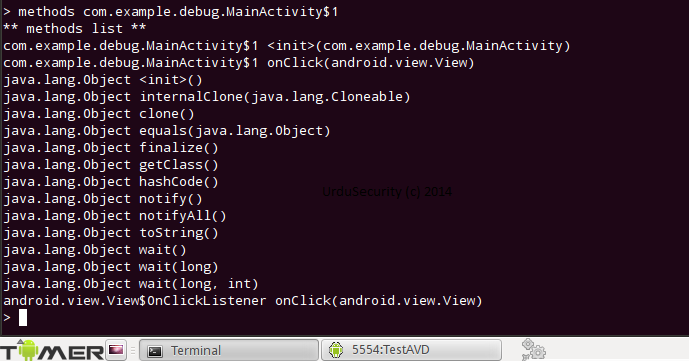
Now Let's Check the classes and methods of Vulnerable.apk and as our main class is com.example.debug.MainActivity$1 so we'll be checking the Methods of that class also. see below.
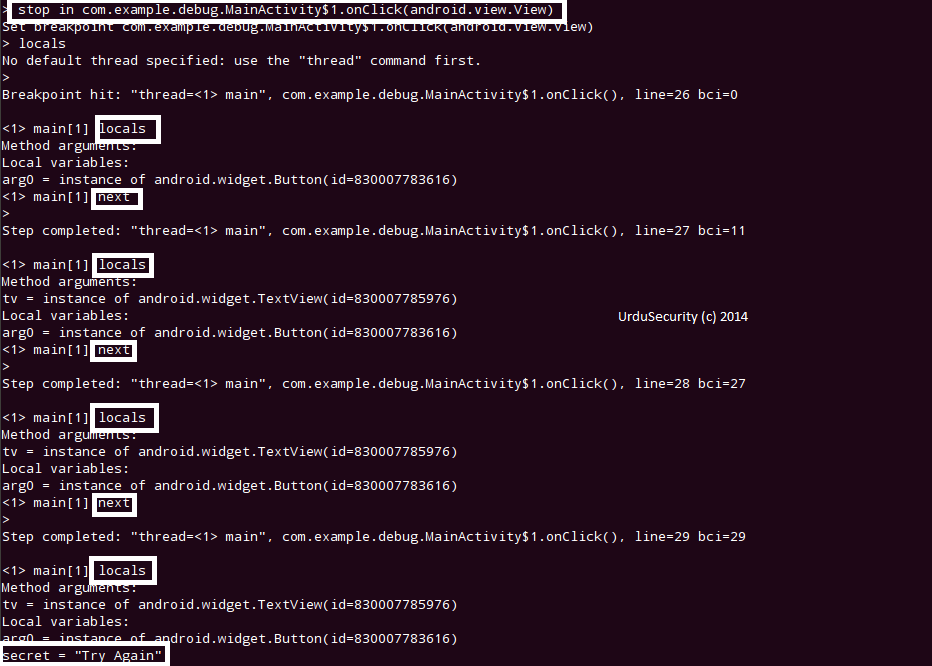
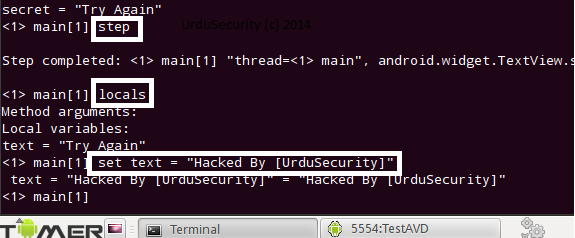
Now We have to set a break point at onClick(android.view.View) method so that we can step through it and exploit the vulnerability by debugging the app.
- stop in com.example.debug.MainActivity$1.onClick(android.view.View)
Please click on the app manually to re run the app as jdb don't provide this functionality here.
as in above figure , You have to step through all the steps untill you get the desired string, as we remember we have to replace Try Again with Hacked By UrduSecurity, so we found that string here. Now its time to step in the secret = "Try Again" String.
and finally its time to give command run , and you'll see that the app will automatically pop up our changed message that is: Hacked By [UrduSecurity].
Yahooooooo, we just hacked the app. We can do a lot of other intresting stuff like getting a remote shell on victim and so on which we'll show you in later tutorials. Hope You've enjoyed this tutorial.
References
- infosecinstitute.com
- androidtamer.com
- oracle.com
- askubuntu.com
Android Hacking: Hacking Debuggable Android Apps
Views:












CLASSIC CYBER HACKS
ReplyDeleteHow well are you prepared for a Cyber incident or Breach?, Is your Data safe?
Strengthen your Cybersecurity stance by contacting CLASSIC CYBER NOTCH @ GMAIL DOT COM for a Perfect, Unique, Classic and Professional Job in Securing your Network against all sort of breaches and from scammers as well.
For we are Specially equipped with the Best hands to getting your Cyber Hack needs met as your jobs will be handled with utmost professionalism.
We do All type of cyber Jobs such as:
☑ TRACKING of GPS location, cars, Computers, Phones (Apple, windows and Android), e.t.c.
We also Track
E-MAIL account,(G-mail, Yahoo mail, AOL, Proton mail, etc.)
SOCIAL MEDIA account, (Facebook, Twitter, Skype, Whatsapp, e.t.c.)
☑ RECOVERY of Passwords for E-mail address, Phones, Computers, Social media Accounts, Documents e.t.c
☑ INSTALLATION of Spy ware so as to spy into someone else's computer, phone or E-mail address and also Installation of Spy ware software on your individual O.S so as to detect intrusion of any type.
We also Create and Install VIRUS into any desired computer gadget.
☑ CRACKING Websites, any desired gadget it computers or phones, CCTV Survelance camera, Data base (of both Private and Govt organization, such as Schools, Hospitals, Court houses, The FBI, NSA) e.t.c....
NOTE:
Other Jobs we do are:
☑ We provide Private Investigator service
☑ Clearing Criminal records of diverse type
☑ Binary Options fraud Recovery
☑ Bitcoin Mining
☑ Issuing of Blank ATM cards
☑ And many more... etc.
We assure you that your Job will be attended to with care and efficiency as it will be handled by the Best professional hands in Cyber literacy.
We also have a forum where you can get yourself equipped with Advanced hacking Knowledge..
CLASSIC CYBER HACKS gives you the Best service in the Hacking world as our Success rate is Top Notch
Be sure to 📱 💻 us via E-mail @
Classic cyber notch at gmail dot com
any time, any day to get the Best Professional hands involved in putting a smile on your face.
We're Classic Hacks
Signed,
Collins .A.
Hello everyone..
DeleteI'm selling US leads. Details in leads are:
Full Name
SSN
DOB
Phone Numbers
Address
City
State
Zip
Residential Status
Account Number
DL number
Emails
All leads are genuine & fresh, I will provide you samples for checking if u want.
Dealing in almost all types of leads:
SSN Leads
Dead Fullz
Premium Leads
Mortgage Leads
Bank Account Leads
Employee Leads
Business Leads
Home Owners Leads
DL Leads
Emails Leads
Phone Numbers Leads
Each lead will b cost $1
Also cvv Fullz available track 1 & track 2 with pin.
Interested person contact, scammers stay away, sampling is free of cost.
email > leads.sellers1212@gmail.com
Whatsapp > +923172721122
Telegram > @leadsupplier
ICQ > 752822040
Web Security >>>>> Download Now
Delete>>>>> Download Full
Web Security >>>>> Download LINK
>>>>> Download Now
Web Security >>>>> Download Full
>>>>> Download LINK ZB
Hello everyone..
ReplyDeleteI'm selling US leads. Details in leads are:
Full Name
SSN
DOB
Phone Numbers
Address
City
State
Zip
Residential Status
Account Number
DL number
Emails
All leads are genuine & fresh, I will provide you samples for checking if u want.
Dealing in almost all types of leads:
SSN Leads
Dead Fullz
Premium Leads
Mortgage Leads
Bank Account Leads
Employee Leads
Business Leads
Home Owners Leads
DL Leads
Emails Leads
Phone Numbers Leads
Each lead will b cost $1
Also cvv Fullz available track 1 & track 2 with pin.
Interested person contact, scammers stay away, sampling is free of cost.
email > leads.sellers1212@gmail.com
Whatsapp > +923172721122
Telegram > @leadsupplier
ICQ > 752822040
Hello all
ReplyDeleteam looking few years that some guys comes into the market
they called themselves hacker, carder or spammer they rip the
peoples with different ways and it’s a badly impact to real hacker
now situation is that peoples doesn’t believe that real hackers and carder scammer exists.
Anyone want to make deal with me any type am available but first
I‘ll show the proof that am real then make a deal like
Available Services
..Wire Bank Transfer all over the world
..Western Union Transfer all over the world
..Credit Cards (USA, UK, AUS, CAN, NZ)
..School Grade upgrade / remove Records
..Spamming Tool
..keyloggers / rats
..Social Media recovery
.. Teaching Hacking / spamming / carding (1/2 hours course)
discount for re-seller
Contact: 24/7
fixitrogers@gmail.com
Hi All!
ReplyDeleteI'm selling fresh & genuine SSN Leads, with good connectivity. All data is tested & verified.
Headers in Leads:
First Name | Last Name | SSN | Dob | Address | State | City | Zip | Phone Number | Account Number | Bank NAME | DL Number | House Owner
*You can ask for sample before any deal
*Each SSN lead will be cost $1
*Premium Lead will be cost $5
*If anyone wants in bulk I will negotiate
*Sampling is just for serious buyers
Hope for the long term deal
For detailed information please contact me on:
Whatsapp > +923172721122
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
RELIABLE PRIVATE ONLINE INVESTIGATIONS:wizardcyprushacker@gmail.com WhatsApp +1 (424) 209-7204, Have you ever needed an expert when it comes to hacking? Have you ever wanted to hack someone’s email account? Recover lost accounts,school grade,boost credit score? Do you need to find a person’s sensitive information? Do you want to invade a person’s PayPal,Bitcoin hack,and recovery Skills, Amazon, Facebook or any other site account? Upgrade of University Grades,Password and email Retrieval, phone Lines monitoring, Skype Accounts, Hack Social Network, Trace calls on real time conversations, Remove Criminal Records, Credit Fixing, cyber-crime investigation, Hack Bank Accounts, Identification of Cheating Partner or employee,GET HOT STOCK TIPS..
ReplyDeleteThen contact Email:-wizardcyprushacker@gmail.com WhatsApp +1 (424) 209-7204
he won't under any circumstances work for free
I was searching for loan to sort out my bills& debts, then i saw comments about a programmed cloned ATM card that can be used to hack and withdraw money from any ATM machines around you . I doubted at first but thus decided to give it a try by contacting {skylinktechnes@yahoo.com} they responded with their guidelines on how the card works. I was assured that the card can withdraw $5,000 instant per day & was credited with $50,000 so i requested for one & paid the delivery fee to obtain the card, i was shocked to see the UPS agent in my resident with a parcel{card} i signed and went back inside and confirmed the card work's after the agent left. This is no doubts because i have the card & has made used of the card. This hackers are USA based hackers set out to help people with financial freedom!! Contact these email if you wants to get rich with this Via email skylinktechnes@yahoo.com whatsapp/t: +1(213)785-1553
ReplyDeleteWeb Security >>>>> Download Now
ReplyDelete>>>>> Download Full
Web Security >>>>> Download LINK
>>>>> Download Now
Web Security >>>>> Download Full
>>>>> Download LINK
I would like to give my gratitude to Wizard James Services because this site is the only one where there is nothing superfluous going on, they were completely honest and transparent all the way through. They said they could crack my wallet, it took them 4 hours and they took their 20% and left me the rest, Job well done. His contact: wizardjamesrecovery@usa.com or WhatsApp: +1 (863) 254-2842
ReplyDelete